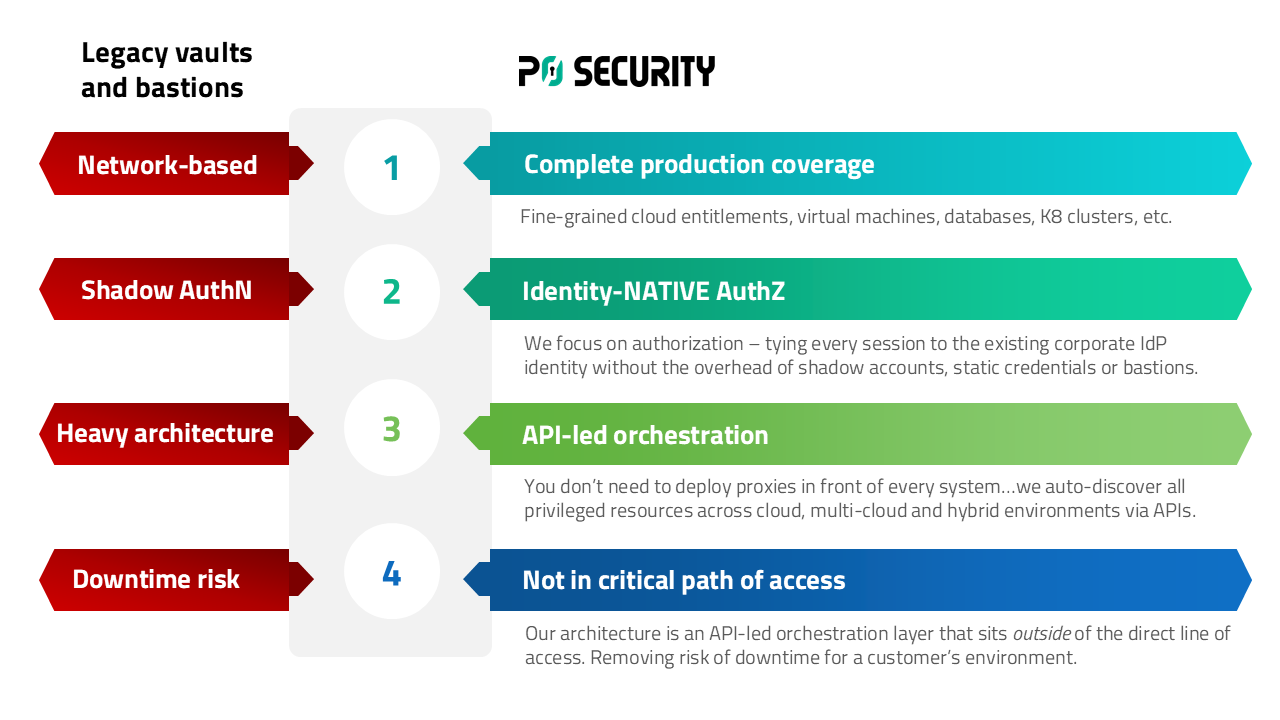
Centralize and scale zero standing privilege to any sensitive resource with the P0 AuthZ Control Plane























NO VAULTS, STATIC CREDENTIALS, BASTIONS OR MANUAL WORKFLOWS
P0’s Authorization Control Plane powers ZSP for every user, NHI, and agent. With centralized visibility, just enough privilege and just-in-time controls, P0 customers enjoy end-to-end production access security that keeps pace with development.
Extend PAM to multi-cloud and hybrid environments with a central access control plane for all users, NHIs and agents.